(See also the personal webpage of our group members)
(For a full list of publications, see below, and see also the personal webpage of our group members)
Networked Control Systems (NCSs) are integral to many critical infrastructures such as power grids, transportation, and production systems. The resilient operation of such NCS against cyber-attacks is essential for society, and risk management presents an effective framework for addressing these security challenges. The risk management framework encompasses two steps: risk assessment and risk mitigation. The risk assessment step aims to quantify the risk, whereas the risk mitigation step focuses on designing mitigation strategies. This thesis leverages the risk management framework to analyze and design NCSs that are resilient to cyber-attacks. In particular, this thesis aims to address the following research challenges. Firstly, we aim to assess the risk of attack scenarios that are realistic (risk assessment step). In particular, we consider adversaries and operators with different levels of knowledge about the NCS. For instance, an adversary or operator may possess complete knowledge of the system dynamics or have only partial knowledge with varying degrees of uncertainty. Hence, we describe a systematic approach to assess the risk considering the interplay between the knowledge levels of adversaries and operators. Secondly, we aim to design the NCS to minimize the risk of attacks (risk mitigation step). We explore three different strategies to minimize the risk: (a) controller/detector design, (b) security measure allocation, and (c) system architecture design. In the first strategy, we design the controller and detector gains to minimize the risk of attacks. Here, risk is characterized by the performance loss caused by stealthy attacks on the NCS. In the second strategy, we consider a distributed NCS where certain distributed devices can be secured from attacks by deploying secure sensors and actuators. Then, we aim to strategically determine the devices to secure and mitigate the risk of attacks effectively. Finally, inspired by digital watermarking, we explore the idea of introducing watermarks in NCS to detect attacks efficiently. Throughout the thesis, we provide various numerical examples to depict the efficacy of risk assessment and risk mitigation algorithms. We also provide numerous discussions and avenues for future research directions.
Sribalaji Coimbatore Anand
Doctoral Thesis, Uppsala University, (2024)
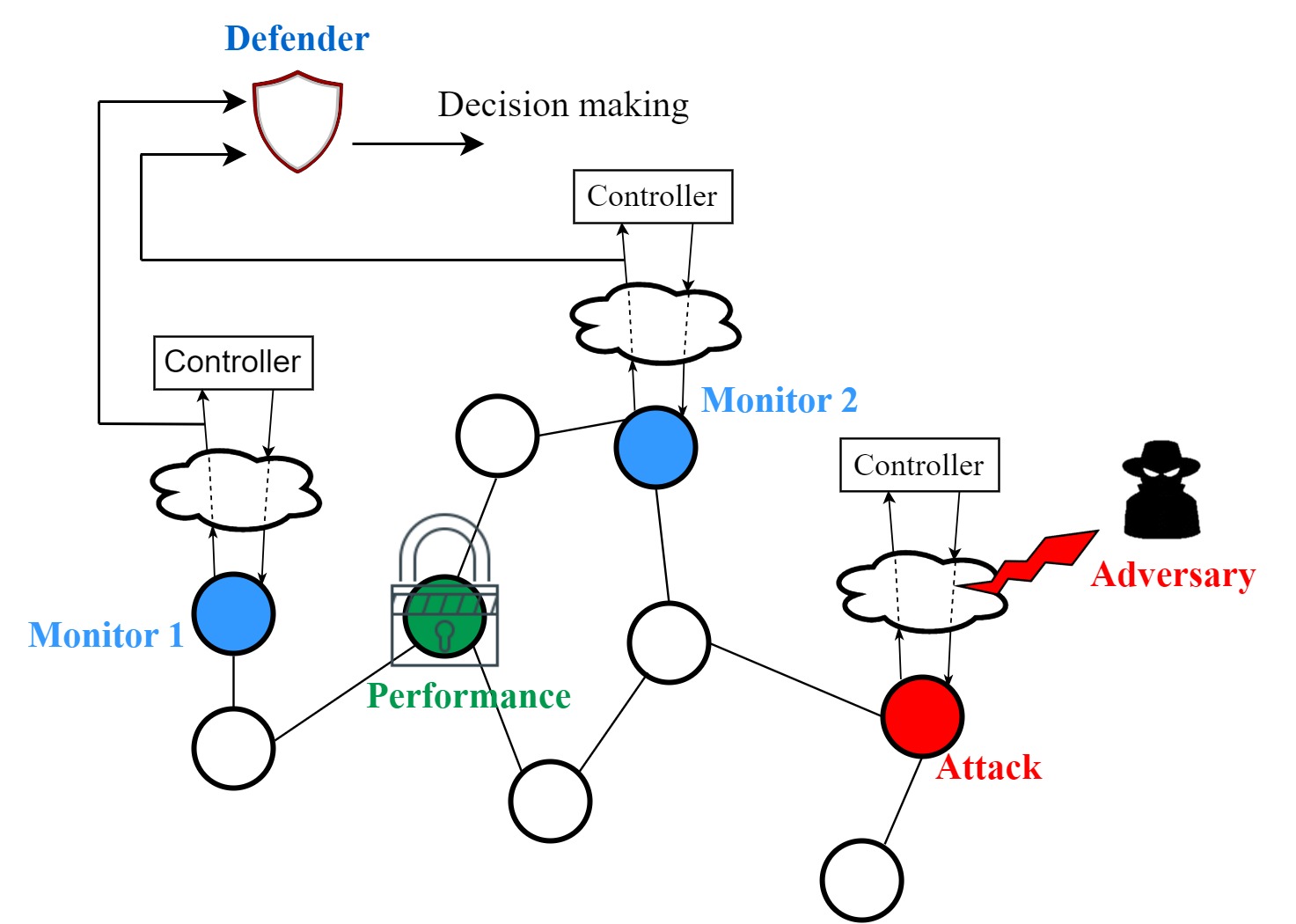
This thesis develops a framework for evaluating and improving the security of networked control systems in the face of cyber attacks. The considered security problem involves two strategic agents, namely a malicious adversary and a defender, pursuing their specific and conflicting goals. The defender aims to efficiently allocate defense resources with the purpose of detecting malicious activities. Meanwhile, the malicious adversary simultaneously conducts cyber attacks and remains stealthy to the defender. We tackle the security problem by proposing a game-theoretic framework and characterizing its main components the payoff function, the action space, and the available information for each agent. Especially, the payoff function is characterized based on the output-to-output gain security metric that fully explores the worst-case attack impact. Then, we investigate the properties of the game and how to efficiently compute its equilibrium. Given the combinatorial nature of the defender actions, one important challenge is to alleviate the computational burden. To overcome this challenge, the thesis contributes several system- and graph-theoretic conditions that enable the defender to shrink the action space, efficiently allocating the defense resources. The effectiveness of the proposed framework is validated through numerical examples.
Anh Tung Nguyen
Licentiate Thesis, Uppsala University, (2023)

This book presents an in-depth overview of recent work related to the safety, security, and privacy of cyber-physical systems (CPSs). It brings together contributions from leading researchers in networked control systems and closely related fields to discuss overarching aspects of safety, security, and privacy; characterization of attacks; and solutions to detecting and mitigating such attacks.
The book begins by providing an insightful taxonomy of problems, challenges and techniques related to safety, security, and privacy for CPSs. It then moves through a thorough discussion of various control-based solutions to these challenges, including cooperative fault-tolerant and resilient control and estimation, detection of attacks and security metrics, watermarking and encrypted control, privacy and a novel defense approach based on deception. The book concludes by discussing risk management and cyber-insurance challenges in CPSs, and by presenting the future outlook for this area of research as a whole.
Its wide-ranging collection of varied works in the emerging fields of security and privacy in networked control systems makes this book a benefit to both academic researchers and advanced practitioners interested in implementing diverse applications in the fields of IoT, cooperative autonomous vehicles and the smart cities of the future.
Riccardo M. G. Ferrari and André M. H. Teixeira (Eds)
@article{Anand_Review2026,
author = {Anand, S. C. and Nguyen, A. T. and Teixeira, A. M. H. and Sandberg, H. and Johansson, K. H.},
journal = {Annual Reviews in Control (Submitted)},
title = {Quantifying Security for Networked Control Systems: A Review},
published = {0},
tag = {10001}
}@article{Arnstrom_SCL2025,
author = {Arnstr\"{o}m, D. and Teixeira, A. M. H.},
journal = {System \& Control Letters (Submitted)},
volume = {},
number = {},
pages = {},
title = {Efficiently Computing the Cyclic Output-to-Output Gain},
year = {},
published = {0},
tag = {10005}
}@inproceedings{Eriksson_ECC026,
author = {Eriksson, L. and Wigren, T. and Zachariah, D. and Teixeira, A. M. H.},
title = {Detecting Feedback-path Delay Injection Attacks Using Interacting Multiple Model Filtering},
booktitle = {ECC (Submitted)},
published = {0},
year = {},
tag = {}
}@inproceedings{Seifullaev_IFACWC2026,
author = {Seifullaev, R. and Teixeira, A. M. H.},
title = {Impact analysis of hidden faults in nonlinear control systems using output-to-output gain},
booktitle = {IFAC World Congress (Submitted)},
published = {0},
year = {},
tag = {10005}
}@inproceedings{Seifullaev_ECC2026,
author = {Seifullaev, R. and Teixeira, A. M. H.},
title = {An H2-norm approach to performance analysis of networked control systems under multiplicative routing transformations},
booktitle = {European Control Conference (Submitted)},
published = {0},
year = {},
tag = {10005}
}@article{Ramos_TAC2025,
author = {Ramos, G. and Silvestre, D. and Teixeira, A. M. H. and Pequito, S.},
journal = {IEEE Trans. Automatic Control (Submitted)},
number = {},
pages = {},
title = {Accurate Average Consensus with Joint Resilience and Privacy Guarantees},
volume = {},
year = {},
published = {0},
tag = {10006}
}@article{Gallo_TAC2025,
author = {Gallo, A. and Nguyen, A. T. and Oliva, G. and Teixeira, A. M. H.},
journal = {IEEE Trans. Automatic Control (Submitted)},
number = {},
pages = {},
title = {On the Boundedness of the Solution to the Output-to-output l2-gain Strategic Stealthy Attacks Problem},
volume = {},
year = {},
published = {0},
tag = {10005}
}@article{Li_TAC2025,
author = {Li, Z. and Nguyen, A. T. and Teixeira, A. M. H. and Mo, Y. and Johansson, K. H.},
journal = {IEEE Trans. Automatic Control (Submitted)},
title = {Secure Filtering against Spatio-Temporal False Data Attacks under Asynchronous Sampling},
published = {0},
tag = {}
}@article{Dong_TCST2025,
author = {Dong, Jingwei and Sadabadi, Mahdieh S. and Mattsson, Per and Teixeira, Andr\'{e}},
journal = {IEEE Trans. Control System Technology (Submitted)},
volume = {},
number = {},
pages = {},
title = {Distributed Multiple Fault Detection and Estimation in DC Microgrids with Unknown Power Loads},
year = {},
published = {0},
tag = {}
}@article{Zafar_TDSC2025,
title = {Robust Federated Learning Against Poisoning Attacks: A GAN-Based Defense Framework},
journal = {(In preparation)},
author = {Zafar, Usama and Teixeira, André M. H. and Toor, Salman},
year = {},
published = {0},
tag = {10003}
}@inproceedings{Parsa_ICLR2026,
author = {Parsa, J. and Daghestani, A. H. and Teixeira, A. M. H. and Johansson, M.},
title = {Byzantine-Robust Federated Learning with Learnable Aggregation Weights},
booktitle = {ICLR 2026 (Accepted)},
published = {1},
year = {2026},
tag = {10003},
}@inproceedings{Dong_ACC2026,
author = {Dong, J. and Zhang, K. and Nguyen, A. T. and Teixeira, A. M. H.},
title = {Fundamental limitations of sensitivity metrics for anomaly impact analysis in LTI systems},
booktitle = {American Control Conference (Accepted)},
published = {1},
year = {2026},
tag = {10005}
}@article{Nguyen_TAC2026,
author = {Nguyen, A. T. and Anand, S. C. and Teixeira, A. M. H.},
journal = {IEEE Trans. Automatic Control (Accepted)},
title = {Scalable and Optimal Security Allocation in Networks against Stealthy Injection Attacks},
published = {1},
year = {2026},
doi = {10.1109/TAC.2025.3639126},
tag = {10005},
taga = {10001}
}@inproceedings{Zhang_CDC2025,
author = {Zhang, Kangkang and Kasis, Andreas and Teixeira, A. M. H. and Jiang, Bin},
title = {Vulnerability Analysis against Stealthy Integrity Attacks for Nonlinear Systems},
booktitle = {IEEE Conf. on Decision and Control (CDC)},
published = {1},
year = {2025},
tag = {10005}
}@inproceedings{Nguyen_CDC2025,
author = {Nguyen, A. T. and Zhu, Q. and Teixeira, A. M. H.},
title = {Bilateral Cognitive Security Games in Networked Control Systems under Stealthy Injection Attacks},
booktitle = {IEEE Conf. on Decision and Control (CDC)},
published = {1},
year = {2025},
tag = {}
}@article{Tosun_EJC2025,
author = {Tosun, F. E. and Teixeira, A. M. H. and Dong, J. and Ahlén, A. and Dey, S.},
journal = {European Journal of Control},
volume = {},
number = {},
pages = {101427},
title = {Kullback-Leibler Divergence-Based Filter Design Against Bias Injection Attacks},
year = {2025},
published = {1},
doi = {10.1016/j.ejcon.2025.101427},
tag = {10002}
}@inproceedings{Nguyen_NecSys2025,
author = {Nguyen, A. T. and Anand, S. C. and Teixeira, A. M. H.},
title = {Security Metrics for Uncertain Interconnected Systems under Stealthy Data Injection Attacks},
booktitle = {10th IFAC Conference on Networked Systems (NecSys)},
published = {1},
year = {2025},
tag = {10005}
}@inproceedings{Arnstrom_L4DC2025,
author = {Arnstr\"{o}m, D. and Teixeira, A. M. H.},
title = {Data-Driven and Stealthy Deactivation of Safety Filters},
booktitle = {Annual Learning for Dynamics & Control Conference (L4DC)},
published = {1},
year = {2025},
tag = {10005}
}@inproceedings{Anand_ECC2025,
author = {Anand, S. C. and Chong, M. S. and Teixeira, A. M. H.},
title = {Data-Driven Identification of Attack-free Sensors in Networked Control Systems},
booktitle = {European Control Conference},
published = {1},
year = {2025},
tag = {10005}
}@article{Gallo_Automatica2025,
author = {Gallo, A. J. and Anand, S. C. and Teixeira, A. M. H. and Ferrari, R. M.G.},
journal = {Automatica},
title = {Switching Multiplicative Watermark design against Covert Attacks},
volume = {177},
pages = {112301},
year = {2025},
published = {1},
doi = {10.1016/j.automatica.2025.112301},
tag = {10001}
}@article{Tosun_TIFS2025,
author = {Tosun, F. E. and Teixeira, A. M. H. and Dong, J. and Ahlén, A. and Dey, S.},
journal = {IEEE Trans. Information Forensics and Security},
volume = {20},
number = {},
pages = {2763-2777},
title = {Kullback-Leibler Divergence-Based Observer Design Against Sensor Bias Injection Attacks in Single-Output Systems},
year = {2025},
published = {1},
tag = {10002},
doi = {10.1109/TIFS.2025.3546167}
}@article{Nguyen_TCNS2024,
author = {Nguyen, A. T. and Teixeira, A. M. H. and Medvedev, A.},
journal = {IEEE Trans. Control of Network Systems},
title = {Security Allocation in Networked Control Systems under Stealthy Attacks},
volume = {12},
number = {1},
pages = {216-227},
doi = {10.1109/TCNS.2024.3462546},
month = mar,
year = {2025},
published = {1},
tag = {10005}
}@inproceedings{Nguyen_CRITIS24,
author = {Nguyen, A. T. and Hertzberg, A. and Teixeira, A. M. H.},
title = {Centrality-based Security Allocation in Networked Control Systems},
year = {2025},
editor = {Oliva, Gabriele and Panzieri, Stefano and H{\"a}mmerli, Bernhard and Pascucci, Federica and Faramondi, Luca},
booktitle = {Critical Information Infrastructures Security},
publisher = {Springer Nature Switzerland},
address = {Cham},
pages = {212--230},
note = {Presented at the 19th International Conference on Critical Information Infrastructures Security},
doi = {10.1007/978-3-031-84260-3_13},
published = {1},
tag = {10005}
}@inproceedings{Ju2024,
author = {Ju, L. and Zhang, T. and Toor, S. and Hellander, A.},
booktitle = {IEEE Transactions on Machine Learning in Communications and Networking},
title = {Accelerating Fair Federated Learning: Adaptive Federated Adam},
pages = {1017-1032},
volume = {2},
published = {1},
year = {2024},
doi = {10.1109/TMLCN.2024.3423648},
tag = {10003}
}@inproceedings{Anand_CDC024,
author = {Anand, S. C. and Grussler, C. and Teixeira, A. M. H.},
title = {Scalable metrics to quantify security of large-scale systems},
year = {2024},
booktitle = {IEEE Conference on Decisions and Control},
doi = {10.1109/CDC56724.2024.10886808},
published = {1},
tag = {10001}
}@inproceedings{Seifullaev_CDC024,
author = {Seifullaev, R. and Teixeira, A. M. H. and Ahl\'{e}n, A.},
booktitle = {IEEE Conference on Decisions and Control},
title = {Event-triggered control of nonlinear systems under deception and Denial-of-Service attacks},
year = {2024},
doi = {10.1109/CDC56724.2024.10886155},
published = {1},
tag = {10004}
}@inproceedings{Sun_ARES2024,
author = {Sun, Z. and Teixeira, A. M. H. and Toor, S.},
booktitle = {The International Conference on Availability, Reliability and Security (ARES)},
title = {GNN-IDS: Graph Neural Network based Intrusion Detection System},
year = {2024},
doi = {10.1145/3664476.3664515},
published = {1}
}@inproceedings{Arnstrom_ECC2024,
author = {Arnstr\"{o}m, D. and Teixeira, A. M. H.},
booktitle = {European Control Conference},
title = {Stealthy Deactivation of Safety Filters},
year = {2024},
published = {1}
}@inproceedings{Wigren_ECC2024,
author = {Wigren, T. and Teixeira, A. M. H.},
booktitle = {European Control Conference},
title = {Delay Attack and Detection in Feedback Linearized Control Systems},
year = {2024},
published = {1},
tag = {10004}
}@inproceedings{Wigren_ECC2025,
author = {Wigren, T.},
booktitle = {European Control Conference},
title = {Convergence in delayed recursive identification of nonlinear systems},
year = {2024},
published = {1},
tag = {10004}
}@inproceedings{Tosun_SAFEPROCESS2024,
author = {Tosun, F. E. and Teixeira, A. M. H. and Ahlén, A. and Dey, S.},
booktitle = {12th IFAC Symposium on Fault Detection, Supervision and Safety for Technical Processes},
title = {Kullback-Leibler Divergence-Based Detector Design Against Bias Injection Attacks in an Artificial Pancreas System},
year = {2024},
published = {1},
doi = {10.1016/j.ifacol.2024.07.269},
tag = {10002}
}@article{Tosun_JPC2024,
author = {Tosun, F. E. and Teixeira, A. M. H. and Abdalmoaty, M. and Ahl\'{e}n, A. and Dey, S.},
journal = {Journal of Process Control},
volume = {153},
number = {103162},
title = {Quickest Detection of Bias Injection Attacks on the Glucose Sensor in the Artificial Pancreas Under Meal Disturbances},
year = {2024},
doi = {10.1016/j.jprocont.2024.103162},
published = {1},
tag = {10002}
}@article{Anand_TAC2024,
author = {Anand, S. C. and Teixeira, A. M. H. and Ahl\'{e}n, A.},
journal = {IEEE Trans. Automatic Control},
number = {5},
pages = {3214--3221},
title = {Risk Assessment of Stealthy Attacks on Uncertain Control Systems},
volume = {69},
month = may,
year = {2024},
doi = {10.1109/TAC.2023.3318194},
published = {1},
tag = {10001}
}@phdthesis{Nguyen_Lic2023,
author = {Nguyen, Anh Tung},
title = {Security Allocation in Networked Control Systems},
school = {Uppsala University},
year = {2023},
address = {Uppsala, Sweden},
month = oct,
type = {Licentiate thesis},
tag = {10005}
}@article{Ramos_TAC2024,
author = {Ramos, G. and Aguiar, A. P. and Kar, Soummya and Pequito, S.},
journal = {IEEE Trans. Automatic Control (Accepted)},
title = {Privacy preserving average consensus through network augmentation},
year = {2023},
published = {1},
tag = {10006}
}@article{Ramos_CSL2024,
author = {Ramos, G. and Pequito, S.},
journal = {Systems & Control Letters},
volume = {180},
pages = {105608},
year = {2023},
title = {Designing communication networks for discrete-time consensus for performance and privacy guarantees},
doi = {10.1016/j.sysconle.2023.105608},
published = {1},
tag = {10006}
}@article{Anand_IEEEOJCSys2023,
author = {Anand, S. C. and Teixeira, A. M. H.},
journal = {IEEE Open Journal of Control Systems},
number = {},
pages = {297--309},
title = {Risk-based Security Measure Allocation Against Actuator Attacks},
volume = {2},
year = {2023},
doi = {10.1109/OJCSYS.2023.3305831},
published = {1},
tag = {10001}
}@inproceedings{Ramos_CDC2023,
author = {Ramos, G. and Teixeira, A. M. H. and Pequito, S.},
booktitle = {IEEE Conference on Decisions and Control},
title = {On the trade-offs between accuracy, privacy, and resilience in average consensus algorithms},
year = {2023},
published = {1},
tag = {10005},
taga = {10006}
}@inproceedings{Tosun_CDC2023,
address = {},
author = {Tosun, F. E. and Teixeira, A. M. H.},
booktitle = {IEEE Conference on Decisions and Control},
title = {Robust Sequential Detection of Non-stealthy Sensor Deception Attacks in an Artificial Pancreas System},
year = {2023},
published = {1},
tag = {10002}
}@inproceedings{Li_CDC2023,
address = {},
author = {Li, Z. and Nguyen, A. T. and Teixeira, A. M. H. and Mo, Y. and Johansson, K. H.},
booktitle = {IEEE Conference on Decisions and Control},
title = {Secure State Estimation with Asynchronous Measurements against Malicious Measurement-data and Time-stamp Manipulation},
year = {2023},
published = {1},
tag = {10005}
}@inproceedings{Wigren_CDC2023,
address = {},
author = {Wigren, T. and Teixeira, A. M. H.},
booktitle = {IEEE Conference on Decisions and Control},
title = {Feedback Path Delay Attacks and Detection},
year = {2023},
published = {1},
tag = {10004}
}@article{Naha_AUTOMATICA2023,
author = {Naha, A. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
journal = {Automatica},
number = {},
pages = {111147},
title = {Quickest Detection of Deception Attacks on Cyber-Physical Systems with a Parsimonious Watermarking Policy},
volume = {155},
year = {2023},
doi = {10.1016/j.automatica.2023.111147},
}@article{Chockalingam_JISA2023,
author = {Chockalingam, S. and Pieters, W. and Teixeira, A. M. H. and van Gelder, P.},
journal = {Journal of Information Security and Applications},
number = {},
title = {Probability Elicitation for Bayesian Networks to Distinguish between Intentional Attacks and Accidental Technical Failures},
year = {2023},
doi = {10.1016/j.jisa.2023.103497},
volume = {75},
pages = {103497},
issn = {2214-2126}
}@article{Naha_EJC2023,
author = {Naha, A. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
journal = {European Journal of Control},
number = {},
pages = {100804},
title = {Quickest Physical Watermarking-Based Detection of Measurement Replacement Attacks in Networked Control Systems},
volume = {71},
year = {2023},
doi = {10.1016/j.ejcon.2023.100804}
}@inproceedings{AbdalmoatyIFAC2023,
address = {},
author = {Abdalmoaty, M. and Anand, S. C. and Teixeira, A. M. H.},
booktitle = {IFAC World Congress},
title = {Privacy and Security in Network Controlled Systems via Dynamic Masking},
year = {2023},
video = {https://youtu.be/uuz5ppriWLk},
tag = {10006}
}@inproceedings{NguyenIFAC2023,
address = {},
author = {Nguyen, A. T. and Anand, S. C. and Teixeira, A. M. H. and Medvedev, A.},
booktitle = {IFAC World Congress},
title = {Optimal Detector Placement in Networked Control Systems under Cyber-attacks with Applications to Power Networks},
tag = {10005},
year = {2023},
}@inproceedings{WigrenIFAC2023,
address = {},
author = {Wigren, T. and Teixeira, A. M. H.},
booktitle = {IFAC World Congress},
title = {On-line Identification of Delay Attacks in Networked Servo Control},
year = {2023},
tag = {10004}
}@article{Zhang_TAC2023,
author = {Zhang, Q. and Liu, K. and Teixeira, A. M. H. and Li, Y. and Chai, S. and Xia, Y.},
journal = {IEEE Trans. Automatic Control},
number = {6},
pages = {3672--3679},
title = {An Online Kullback-Leibler Divergence-Based Stealthy Attack against Cyber-Physical Systems},
volume = {68},
year = {2023},
doi = {10.1109/TAC.2022.3192201}
}@article{NahaTAC2022,
author = {Naha, A. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
journal = {IEEE Trans. Automatic Control},
number = {3},
pages = {1941--1948},
title = {Sequential detection of Replay attacks},
volume = {68},
year = {2023},
doi = {10.1109/TAC.2022.3174004}
}@inproceedings{NguyenCDC2022,
address = {},
author = {Nguyen, A. T. and Anand, S. C. and Teixeira, A. M. H.},
booktitle = {IEEE Conference on Decision and Control (CDC)},
title = {A Zero-Sum Game Framework for Optimal Sensor Placement in Uncertain Networked Control Systems under Cyber-Attacks},
year = {2022},
doi = {10.1109/CDC51059.2022.9992468},
tag = {10005}
}@inproceedings{NahaCDC2022,
address = {},
author = {Naha, A. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
booktitle = {IEEE Conference on Decisions and Control (CDC)},
title = {Structural analyses of a parsimonious watermarking policy
for data deception attack detection in networked control systems},
year = {2022},
doi = {10.1109/CDC51059.2022.9993201}
}@inproceedings{AnandCCTA2022,
address = {},
author = {Anand, S. C. and Teixeira, A. M. H. and Ahl\'{e}n, A.},
booktitle = {IEEE Conference on Control Technology and Applications (CCTA)},
title = {Risk assessment and optimal allocation of security measures under stealthy false data injection attacks},
year = {2022},
tag = {10001},
doi = {10.1109/CCTA49430.2022.9966025},
}@inproceedings{NguyenNecsys2022,
address = {},
author = {Nguyen, A. T. and Teixeira, A. M. H. and Medvedev, A.},
booktitle = {IFAC Conference on Networked Systems (NecSys)},
title = {A Single-Adversary-Single-Detector Zero-Sum Game in Networked Control Systems},
year = {2022},
doi = {10.1016/j.ifacol.2022.07.234},
tag = {10005},
}@inproceedings{Tosun_ACC2022,
address = {Atlanta, Georgia, USA},
author = {Tosun, F. E. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
booktitle = {American Control Conference},
title = {Detection of Bias Injection Attacks on the Glucose Sensor in the Artificial Pancreas Under Meal Disturbances},
year = {2022},
doi = {10.23919/ACC53348.2022.9867556},
tag = {10002},
}@inproceedings{Naha_ACC2022,
address = {Atlanta, Georgia, USA},
author = {Naha, A. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
booktitle = {American Control Conference},
title = {Sequential Detection of Replay Attacks with a Parsimonious Watermarking Policy},
year = {2022},
doi = {10.23919/ACC53348.2022.9867703},
}@inproceedings{Anand_ACC2022,
address = {Atlanta, Georgia, USA},
author = {Anand, S. C. and Teixeira, A. M. H.},
booktitle = {American Control Conference},
title = {Risk-averse controller design against data injection attacks on actuators for uncertain control systems},
year = {2022},
doi = {10.23919/ACC53348.2022.9867257},
tag = {10001},
}@inproceedings{Ekmefjord_CCGrid2022,
address = {Taormina, Italy},
author = {Ekmefjord, M. and Ait-Mlouk, A. and Alawadi, S. and Åkesson, M. and Singh, P. and Spjuth, O. and Toor, S. and Hellander, A.},
booktitle = {Symposium on Cluster, Cloud and Internet Computing},
title = {Scalable federated machine learning with FEDn},
year = {2022},
doi = {10.1109/CCGrid54584.2022.00065},
tag = {10003},
}@article{Chockalingam_2021,
author = {Chockalingam, S. and Pieters, W. and Teixeira, A. M. H. and van Gelder, P.},
journal = {Cybersecurity},
number = {29},
pages = {},
title = {Bayesian network model to distinguish between intentional attacks and accidental technical failures: a case study of floodgates},
volume = {4},
year = {2021}
}@inproceedings{Gallo_CDC2021,
address = {Austin, Texas, USA},
author = {Gallo, A. J. and Anand, S. C. and Teixeira, A. M. H. and Ferrari, R. M. G.},
booktitle = {IEEE Conf. Decision and Control},
title = {Design of multiplicative watermarking against covert attacks},
year = {2021},
doi = {10.1109/CDC45484.2021.9683075}
}@inproceedings{Anand_CDC2021,
address = {Austin, Texas, USA},
author = {Anand, S. C. and Teixeira, A. M. H.},
booktitle = {IEEE Conf. Decision and Control},
title = {Stealthy Cyber-Attack Design Using Dynamic Programming},
year = {2021},
doi = {10.1109/CDC45484.2021.9683451},
}@inproceedings{Naha_ECC2021,
address = {Rotterdam, The Netherlands},
author = {Naha, A. and Teixeira, A. M. H. and Ahl\'{e}n, A. and Dey, S.},
booktitle = {Eur. Control Conf.},
title = {Deception Attack Detection Using Reduced Watermarking},
year = {2021},
doi = {10.23919/ECC54610.2021.9654843}
}@incollection{FerrariTeixeira_Springer2021,
author = {Ferrari, Riccardo M. G. and Teixeira, Andr{\'e} M. H.},
editor = {Ferrari, Riccardo M.G. and Teixeira, Andr{\'e} M. H.},
title = {Introduction to the Book},
booktitle = {Safety, Security and Privacy for Cyber-Physical Systems},
year = {2021},
publisher = {Springer International Publishing},
address = {Cham},
pages = {1--8},
isbn = {978-3-030-65048-3},
doi = {10.1007/978-3-030-65048-3_1}
}@incollection{Teixeira_Springer2021,
author = {Teixeira, Andr{\'e} M. H.},
editor = {Ferrari, Riccardo M.G. and Teixeira, Andr{\'e} M. H.},
title = {Security Metrics for Control Systems},
booktitle = {Safety, Security and Privacy for Cyber-Physical Systems},
year = {2021},
publisher = {Springer International Publishing},
address = {Cham},
pages = {1--8},
isbn = {978-3-030-65048-3},
doi = {10.1007/978-3-030-65048-3_6},
tag = {10001}
}@incollection{Ferrari_Springer2021,
author = {Ferrari, Riccardo M. G. and Teixeira, Andr{\'e} M. H.},
editor = {Ferrari, Riccardo M.G. and Teixeira, Andr{\'e} M. H.},
title = {Detection of Cyber-Attacks: A Multiplicative Watermarking Scheme},
booktitle = {Safety, Security and Privacy for Cyber-Physical Systems},
year = {2021},
publisher = {Springer International Publishing},
address = {Cham},
pages = {1--8},
isbn = {978-3-030-65048-3},
doi = {10.1007/978-3-030-65048-3_9}
}@inproceedings{Arghavani_WCNC2021,
title = {A {{Game}}-Theoretic {{Approach}} to {{Covert Communications}} in the {{Presence}} of {{Multiple Colluding Wardens}}},
booktitle = {2021 {{IEEE Wireless Communications}} and {{Networking Conference}} ({{WCNC}})},
author = {Arghavani, Abbas and Ahl{\'e}n, Anders and Teixeira, Andr{\'e} and Dey, Subhrakanti},
year = {2021},
month = mar,
pages = {1--7},
issn = {1558-2612},
doi = {10.1109/WCNC49053.2021.9417312},
copyright = {All rights reserved},
keywords = {communications,Computational modeling,Conferences,game-theory,Games,Linear programming,Nash equilibrium,Numerical simulation,Rayleigh channels,security}
}@inproceedings{javed_CBDC2021,
title = {An Evaluation of Container Security Vulnerability Detection Tools},
booktitle = {Cloud and Big Data Computing},
author = {Javed, O. and Toor, S.},
year = {2021},
doi = {10.1145/3481646.3481661},
astract = {Container is a lightweight virtualization technology which packages an application, its dependencies and an operating system (OS) to run as an isolated unit. However, the pressing concern with the use of containers is its susceptibility to security attacks. Consequently, a number of container scanning tools are available for detecting container security vulnerabilities. Therefore, in this experience report, we investigate the quality of existing container scanning tools by considering two metrics that reflect coverage and accuracy. We analyze popular public container images hosted on DockerHub using different container scanning tools (i.e., Clair, Anchore, and Microscanner). Our findings show that existing container scanning tools do not detect application package vulnerabilities. Furthermore, we find that existing tools do not have high accuracy.},
}@article{Rostampour_TAC2020,
author = {Rostampour, V. and Ferrari, R. M.G. and Teixeira, A. M. H. and Keviczky, T.},
journal = {IEEE Trans. Automatic Control},
number = {11},
pages = {5299--5313},
title = {Privatized Distributed Anomaly Detection for Large-Scale Nonlinear Uncertain Systems},
volume = {66},
year = {2021},
doi = {10.1109/TAC.2020.3040251}
}@article{Ferrari_TAC2020,
author = {Ferrari, R. and Teixeira, A. M. H.},
journal = {IEEE Trans. Automatic Control},
number = {6},
pages = {2558--2573},
title = {A Switching Multiplicative Watermarking Scheme for Detection of Stealthy Cyber-Attacks},
volume = {66},
year = {2020}
}@article{Milosevic_TAC2020,
author = {Milosevic, J. and Teixeira, A. M. H. and Sandberg, H. and Johansson, K. H.},
doi = {10.1109/TAC.2020.2981392},
journal = {IEEE Trans. Automatic Control},
number = {9},
pages = {3816--3831},
title = {Actuator Security Indices Based on Perfect Undetectability: Computation, Robustness, and Sensor Placement},
volume = {65},
year = {2020}
}@inproceedings{Anand_2020,
address = {Berlin, Germany},
author = {Anand, S. C. and Teixeira, A M H},
booktitle = {IFAC World Congress},
title = {Joint controller and detector design against
data injection attacks on actuators},
year = {2020}
}@inproceedings{Hylamia_2020,
address = {San Francisco, CA, USA},
author = {Hylamia, S. and Yan, W. and Teixeira, A M. H. and Asan, N. B. and Perez, M. and Augustine, R. and Voigt, T.},
booktitle = {IEEE Workshop on the Internet of Safe Things (SafeThings)},
title = {Privacy-preserving Continuous Tumour Relapse Monitoring Using In-body Radio Signals},
year = {2020}
}@article{Knorn_CSL2019,
author = {Knorn, S. and Teixeira, A. M. H.},
journal = {IEEE Control Systems Letters},
number = {4},
pages = {829--834},
title = {Effects of Jamming Attacks on a Control System With Energy Harvesting},
volume = {3},
year = {2019}
}@inproceedings{Teixeira_CDC2019,
address = {Nice, France},
author = {Teixeira, A. M. H.},
booktitle = {IEEE Conf. Decision and Control},
title = {Optimal stealthy attacks on actuators for strictly proper systems},
year = {2019}
}@inproceedings{Chong_ECC2019,
address = {Napoles, Italy},
author = {Chong, M. S. and Sandberg, H. and Teixeira, A. M. H.},
booktitle = {Eur. Control Conf.},
title = {A Tutorial Introduction to Security and Privacy for Cyber-Physical Systems},
year = {2019}
}@inproceedings{Teixeira_ECC2019,
address = {Napoles, Italy},
author = {Teixeira, A. M. H.},
booktitle = {Eur. Control Conf.},
title = {Data Injection Attacks against Feedforward Controllers},
year = {2019}
}@inproceedings{Umsonst_ACC2019,
address = {Philadelphia, PA, USA},
author = {Umsonst, D. and Nekouei, E. and Teixeira, A. M. H. and Sandberg, H.},
booktitle = {American Control Conf.},
title = {On the Confidentiality of Linear Anomaly Detector States},
year = {2019}
}@article{Pan2018,
archiveprefix = {arXiv},
author = {Pan, Kaikai and Teixeira, Andre M. H. and Cvetkovic, Milos and Palensky, Peter},
doi = {10.1109/TSG.2018.2817387},
eprint = {1708.08349},
issn = {19493053},
journal = {IEEE Trans. Smart Grid},
keywords = {Combined integrity and availability attack,Indexes,Network topology,Power systems,Security,State estimation,Transmission line matrix methods,Transmission line measurements,false data injection,power system state estimation.,risk analysis},
pages = {3044--3056},
volume = {10},
number = {3},
title = {Cyber Risk Analysis of Combined Data Attacks Against Power System State Estimation},
year = {2019},
month = may
}@inproceedings{Chockalingam2018,
address = {Oxford, UK},
author = {Chockalingam, Sabarathinam and Teixeira, Andr{\'{e}} M. H. and Pieters, Wolter and Khakzad, Nima and van Gelder, Pieter},
booktitle = {Proc. 5th Int. Work. Graph. Model. Secur.},
title = {Combining Bayesian Networks and Fishbone Diagrams to Distinguish between Intentional Attacks and Accidental Technical Failures},
year = {2018}
}@inproceedings{Teixeira2018,
address = {Cyprus},
author = {Teixeira, A. M. H. and Ferrari, R. M. G.},
booktitle = {Eur. Control Conf.},
title = {Detection of Sensor Data Injection Attacks with Multiplicative Watermarking},
year = {2018}
}@article{Rostampour2018,
author = {Rostampour, Vahab and Ferrari, Riccardo and Teixeira, Andr{\'{e}} M H and Keviczky, Tam{\'{a}}s},
doi = {10.1016/J.IFACOL.2018.09.703},
issn = {2405-8963},
journal = {IFAC-PapersOnLine},
month = jan,
number = {24},
pages = {975--982},
title = {Differentially-Private Distributed Fault Diagnosis for Large-Scale Nonlinear Uncertain Systems},
volume = {51},
year = {2018}
}@article{Jezdimir2018,
author = {Milo{\v{s}}evi{\'{c}}, Jezdimir and Teixeira, Andr{\'{e}} M. H. and Tanaka, Takashi and Johansson, Karl H. and Sandberg, Henrik},
doi = {10.1002/rnc.4375},
journal = {Int. J. Robust Nonlinear Control},
vol = {30},
number = {11},
pages = {4278--4302},
title = {Security measure allocation for industrial control systems: Exploiting systematic search techniques and submodularity},
year = {2018}
}@article{OsmaniTSC2018,
author = {Osmani, L. and Toor, S. and Komu, N. and Kortelainen, M. and Lindén, T. and White, J. and Khan, R. and Eerola, P. and Tarkoma, S.},
journal = {IEEE Transactions on Services Computing},
number = {},
pages = {},
title = {Secure Cloud Connectivity for Scientific Applications},
volume = {},
year = {2018},
doi = {10.1109/TSC.2015.2469292}
}@article{Teixeira_TCNS_2017,
author = {Teixeira, Andre M. H. and Araujo, Jose and Sandberg, Henrik and Johansson, K.H. Karl H.},
journal = {IEEE Trans. Control Netw. Syst.},
keywords = {Actuators,Computational modeling,Estimation error,Networked control systems,Redundancy},
volume = {5},
number = {4},
pages = {1517-1528},
title = {Distributed sensor and actuator reconfiguration for fault-tolerant networked control systems},
year = {2018}
}@incollection{Chockalingam2017a,
author = {Chockalingam, Sabarathinam and Pieters, Wolter and Teixeira, Andr{\'{e}} M. H. and van Gelder, Pieter},
booktitle = {Secur. IT Syst. Nord. 2017. Lect. Notes Comput. Sci.},
doi = {10.1007/978-3-319-70290-2_7},
editor = {Lipmaa, Helger and and Mitrokotsa, Aikaterini and and Matulevi{\v{c}}ius, Raimundas},
isbn = {9783319702896},
issn = {16113349},
keywords = {Bayesian attack graph,Bayesian network,Cyber security,Information security,Insider threat},
pages = {105--122},
publisher = {Springer, Cham},
title = {Bayesian network models in cyber security: A systematic review},
volume = {10674 LNCS},
year = {2017}
}@inproceedings{Pan2017,
address = {Dresden, Germany},
archiveprefix = {arXiv},
author = {Pan, Kaikai and Teixeira, Andr{\'{e}} M. H. and L{\'{o}}pez, Claudio and Palensky, Peter},
booktitle = {IEEE Int. Conf. Smart Grid Commun.},
doi = {10.1109/SmartGridComm.2017.8340668},
eprint = {1708.08322},
isbn = {9781538640555},
pages = {253--258},
title = {Co-simulation for Cyber Security Analysis: Data Attacks against Energy Management System},
year = {2017}
}@inproceedings{Pan2017a,
address = {Beijing, China},
author = {Pan, Kaikai and Teixeira, Andre M. H. and Cvetkovic, Milos and Palensky, Peter},
booktitle = {IECON 2017 - 43rd Annu. Conf. IEEE Ind. Electron. Soc.},
doi = {10.1109/IECON.2017.8216741},
isbn = {978-1-5386-1127-2},
month = oct,
pages = {4313--4318},
title = {Data attacks on power system state estimation: Limited adversarial knowledge vs. limited attack resources},
year = {2017}
}@article{Ferrari_IFAC_2017,
author = {Ferrari, Riccardo M.G. and Teixeira, Andr{\'{e}} M. H.},
doi = {10.1016/j.ifacol.2017.08.1502},
issn = {24058963},
journal = {IFAC-PapersOnLine},
month = jul,
number = {1},
pages = {7363--7368},
title = {Detection and Isolation of Replay Attacks through Sensor Watermarking},
volume = {50},
year = {2017}
}@inproceedings{Ferrari2017,
address = {Seattle, WA, USA},
author = {Ferrari, Riccardo M.G. and Teixeira, Andre M. H.},
booktitle = {Proc. Am. Control Conf.},
doi = {10.23919/ACC.2017.7963800},
isbn = {9781509059928},
issn = {07431619},
month = may,
pages = {5436--5442},
title = {Detection and isolation of routing attacks through sensor watermarking},
year = {2017}
}@article{Farokhi2017,
author = {Farokhi, Farhad and Teixeira, Andre M. H. and Langbort, Cedric},
doi = {10.1109/TAC.2016.2571779},
issn = {0018-9286},
journal = {IEEE Trans. Automat. Contr.},
keywords = {Estimation,Kalman filtering,game theory,strategic sensors},
month = feb,
number = {2},
pages = {724--739},
title = {Estimation With Strategic Sensors},
volume = {62},
year = {2017}
}@incollection{Chockalingam2017,
archiveprefix = {arXiv},
author = {Chockalingam, Sabarathinam and Hadziosmanovic, Dina and Pieters, Wolter and Teixeira, Andre M. H. and van Gelder, Pieter},
booktitle = {Crit. Inf. Infrastructures Secur. CRITIS 2016. Lect. Notes Comput. Sci.},
doi = {10.1007/978-3-319-71368-7_5},
editor = {Havarneanu, G. and Setola, R. and Nassopoulos, H. and Wolthusen, S.},
eprint = {1707.02140},
isbn = {9783319713670},
issn = {16113349},
keywords = {Integrated safety and security risk assessment,Risk analysis,Risk evaluation,Risk identification,Safety risk assessment,Security risk assessment},
month = oct,
pages = {50--62},
publisher = {Springer, Cham},
title = {Integrated Safety and Security Risk Assessment Methods: A Survey of Key Characteristics and Applications},
year = {2017}
}@article{Ma2017,
author = {Ma, Mingxiao and Teixeira, Andr{\'{e}} M. H. and van den Berg, Jan and Palensky, Peter},
doi = {10.1016/j.ifacol.2017.08.1562},
issn = {24058963},
journal = {IFAC-PapersOnLine},
keywords = {Cyber security,distribution network,risk assessment,stability,voltage control},
month = jul,
number = {1},
pages = {8379--8384},
title = {Voltage Control in Distributed Generation under Measurement Falsification Attacks},
volume = {50},
year = {2017}
}@inproceedings{Pan2016,
address = {Sydney, Australia},
author = {Pan, Kaikai and Teixeira, Andre M H and Cvetkovic, Milos and Palensky, Peter},
booktitle = {IEEE Int. Conf. Smart Grid Commun.},
doi = {10.1109/SmartGridComm.2016.7778773},
isbn = {978-1-5090-4075-9},
month = nov,
pages = {271--277},
title = {Combined data integrity and availability attacks on state estimation in cyber-physical power grids},
year = {2016}
}@inproceedings{Paridari2016a,
address = {Vienna, Austria},
author = {Paridari, K. and Mady, A.E.-D. and {La Porta}, S. and Chabukswar, R. and Blanco, J. and Teixeira, A. M. H. and Sandberg, H. and Boubekeur, M.},
booktitle = {ACM/IEEE 7th Int. Conf. Cyber-Physical Syst. ICCPS},
doi = {10.1109/ICCPS.2016.7479072},
isbn = {9781509017720},
keywords = {Cyber-physical-security,energy management system,resilient control,security analytics,virtual sensor},
title = {Cyber-Physical-Security Framework for Building Energy Management System},
year = {2016}
}@inproceedings{Fichtner2016,
address = {Granby, CO, USA},
author = {Fichtner, Laura and Pieters, Wolter and Teixeira, Andr{\'{e}}},
booktitle = {Proc. 2016 New Secur. Paradig. Work. NSPW},
doi = {10.1145/3011883.3011887},
isbn = {9781450348133},
keywords = {Discourse analysis,Framing,Infrastructure ethnography,Securitization,Security arguments,Security politics,Threat models},
pages = {36--48},
title = {Cybersecurity as a Politikum},
volume = {26-29-Sept},
year = {2016}
}@inproceedings{Wang2016,
address = {San Diego, CA, USA},
author = {Wang, Yuxin and Teixeira, Andr{\'{e}} A.H. and Tian, Yifu and Hulstijn, Joris and Tan, Yao-Hua Y.-H. and Teixeira, Andr{\'{e}} A.H. and Hulstijn, Joris and Tan, Yao-Hua Y.-H.},
booktitle = {22nd Am. Conf. Inf. Syst.},
month = aug,
title = {Fault Detection and Diagnosis for Compliance Monitoring in International Supply Chains},
year = {2016}
}@inproceedings{Sandberg2016,
address = {Vienna, Austria},
author = {Sandberg, Henrik and Teixeira, Andre M.H. A.M.H.},
booktitle = {2016 Sci. Secur. Cyber-Physical Syst. Work.},
doi = {10.1109/SOSCYPS.2016.7580001},
isbn = {978-1-5090-4304-0},
month = apr,
pages = {1--6},
title = {From control system security indices to attack identifiability},
year = {2016}
}@article{Teixeira_Automatica2015,
archiveprefix = {arXiv},
author = {Teixeira, Andr{\'{e}} and Shames, Iman and Sandberg, Henrik and Johansson, Karl Henrik},
doi = {10.1016/j.automatica.2014.10.067},
eprint = {1212.0226},
isbn = {0005-1098},
issn = {00051098},
journal = {Automatica},
keywords = {Attack space,Cyber-physical systems,Secure control systems,System security},
number = {1},
pages = {135--148},
title = {A secure control framework for resource-limited adversaries},
volume = {51},
year = {2015}
}@incollection{Teixeira_BC2015,
author = {Teixeira, Andr{\'{e}} and Kupzog, Friederich and Sandberg, Henrik and Johansson, Karl H.},
booktitle = {Smart Grid Secur. Innov. Solut. a Mod. Grid},
doi = {10.1016/B978-0-12-802122-4.00006-7},
editor = {{Florian Skopik and Paul Smith}},
isbn = {9780128023549},
keywords = {Industrial Control Systems,Resilient Control,Risk Assessment,Security},
pages = {149--183},
publisher = {Elsevier Science Publishing Co Inc},
title = {Cyber-Secure and Resilient Architectures for Industrial Control Systems},
year = {2015}
}@article{Teixeira_CSM_2015,
author = {Teixeira, A and Sou, K and Sandberg, H and Johansson, K},
doi = {10.1109/MCS.2014.2364709},
journal = {IEEE Control Syst. Mag.},
keywords = {Communication networks;Computer crime;Computer sec},
number = {1},
pages = {24--45},
title = {Secure Control Systems: A Quantitative Risk Management Approach},
volume = {35},
year = {2015}
}@inproceedings{Teixeira_CDC2015,
address = {Osaka, Japan},
author = {Teixeira, Andre and Sandberg, Henrik and Johansson, Karl H.},
booktitle = {Proc. IEEE Conf. Decis. Control},
doi = {10.1109/CDC.2015.7402605},
isbn = {9781479978861},
issn = {07431546},
pages = {2582--2587},
title = {Strategic stealthy attacks: The output-to-output ℓ2-gain},
volume = {54rd IEEE},
year = {2015}
}@inproceedings{Teixeira_ETFA2015,
address = {Luxembourg},
author = {Teixeira, Andre and Paridari, Kaveh and Sandberg, Henrik and Johansson, K.H. Karl H.},
booktitle = {2015 IEEE 20th Conf. Emerg. Technol. Fact. Autom.},
doi = {10.1109/ETFA.2015.7301476},
isbn = {978-1-4673-7929-8},
issn = {1946-0740},
keywords = {Inverters,Microgrids,Power system dynamics,Power system stability,Stability analysis,Voltage control,Voltage measurement},
month = sep,
pages = {1--8},
title = {Voltage control for interconnected microgrids under adversarial actions},
year = {2015}
}@inproceedings{Araujo_CDC2014,
address = {Los Angeles, CA, USA},
author = {Ara{\'{u}}jo, Jos{\'{e}} and Teixeira, Andre and Henriksson, Erik and Johansson, Karl H.},
booktitle = {IEEE Conf. Decis. Control},
doi = {10.1109/CDC.2014.7040465},
isbn = {9781467360883},
issn = {07431546},
number = {February},
pages = {6849--6856},
title = {A down-sampled controller to reduce network usage with guaranteed closed-loop performance},
year = {2014}
}@article{Teixeira_Cyb_2014,
author = {Teixeira, A and Shames, I and Sandberg, H and Johansson, K H},
doi = {10.1109/TCYB.2014.2350335},
journal = {IEEE Trans. Cybern.},
number = {11},
pages = {2024--2037},
title = {Distributed Fault Detection and Isolation Resilient to Network Model Uncertainties},
volume = {44},
year = {2014}
}@inproceedings{Farokhi_ACC2014,
address = {Portland, OR, USA},
author = {Farokhi, F and Teixeira, A M H and Langbort, C},
booktitle = {Am. Control Conf.},
doi = {10.1109/ACC.2014.6859123},
month = jun,
pages = {2267--2272},
title = {Gaussian cheap talk game with quadratic cost functions: When herding between strategic senders is a virtue},
year = {2014}
}@inproceedings{Teixeira_ACC2014,
address = {Portland, OR, USA},
author = {Teixeira, A and D{\'{a}}n, G and Sandberg, H and Berthier, R and Bobba, R B and Valdes, A},
booktitle = {Am. Control Conf.},
doi = {10.1109/ACC.2014.6859265},
month = jun,
pages = {4372--4378},
title = {Security of smart distribution grids: Data integrity attacks on integrated volt/{VAR} control and countermeasures},
year = {2014}
}@phdthesis{Teixeira_PhD2014,
author = {Teixeira, Andr\'{e} M. H.},
title = {Toward Cyber-Secure and Resilient Networked Control Systems},
school = {KTH Royal Institute of Technology},
year = {2014},
address = {Stockholm, Sweden},
month = nov
}@inproceedings{teixeirarecon13,
address = {Koblenz, Germany},
author = {Teixeira, A and Ara{\'{u}}jo, J and Sandberg, H and Johansson, K H},
booktitle = {4th {IFAC} Work. Distrib. Estim. Control Networked Syst.},
month = sep,
title = {Distributed actuator reconfiguration in networked control systems},
year = {2013}
}@incollection{Teixeira_Springer2013,
author = {Teixeira, A and Sou, K C and Sandberg, H and Johansson, K H},
booktitle = {Control Cyber-Physical Syst.},
editor = {Tarraf, Danielle C},
number = {449},
pages = {123--142},
publisher = {Springer International Publishing},
series = {Lecture Notes in Control and Information Sciences},
title = {Quantifying Cyber-Security for Networked Control Systems},
year = {2013}
}@article{Shames_NM2012,
author = {Shames, I. and Teixeira, A.M.H. and Sandberg, H. and Johansson, K.H. H},
doi = {10.1109/MNET.2012.6201214},
issn = {08908044},
journal = {{IEEE} Netw. Mag.},
number = {3},
pages = {35--40},
title = {Agents Misbehaving in a Network: a Vice or a Virtue?},
volume = {26},
year = {2012}
}@inproceedings{kn:Teixeira_HICONS2012,
address = {Beijing, China},
author = {Teixeira, Andr{\'{e}} and P{\'{e}}rez, Daniel and Sandberg, Henrik and Johansson, Karl Henrik},
booktitle = {Proc. 1st Int. Conf. High Confid. Networked Syst. - HiCoNS '12},
doi = {10.1145/2185505.2185515},
isbn = {9781450312639},
issn = {00375675},
pages = {55--64},
title = {Attack models and scenarios for networked control systems},
year = {2012}
}@inproceedings{Andersson_2012,
address = {Washington, DC, USA},
author = {Andersson, G and Esfahani, P M and Vrakopoulou, M and Margellos, K and Lygeros, J and Teixeira, A and Dan, G and Sandberg, H and Johansson, K H},
booktitle = {IEEE PES Innov. Smart Grid Technol.},
doi = {10.1109/ISGT.2012.6175543},
pages = {1--2},
title = {Cyber-security of SCADA systems},
year = {2012}
}@inproceedings{kn:Shames2012_ACC,
address = {Montreal, Canada},
author = {Shames, I and Teixeira, A and Sandberg, H and Johansson, K H},
booktitle = {Am. Control Conf.},
month = jun,
title = {Distributed Fault Detection and Isolation with Imprecise Network Models},
year = {2012}
}@article{Shames_SPL2012,
author = {Shames, I and Teixeira, A M H and Sandberg, H and Johansson, K H},
doi = {10.1109/LSP.2012.2217328},
journal = {{IEEE} Signal Process. Lett.},
month = nov,
number = {11},
pages = {749--752},
title = {Fault Detection and Mitigation in Kirchhoff Networks},
volume = {19},
year = {2012}
}@inproceedings{kn:Teixeira_ACC2012,
address = {Montreal, Canada},
author = {Teixeira, A and Sandberg, H and D{\'{a}}n, G and Johansson, K H},
booktitle = {Am. Control Conf.},
title = {Optimal power flow: closing the loop over corrupted data},
year = {2012}
}@inproceedings{Teixeira_Allerton2012,
address = {Monticello, IL, USA},
author = {Teixeira, A. and Shames, I. and Sandberg, H. and Johansson, K.H. H},
booktitle = {50th Annu. Allert. Conf. Commun. Control. Comput.},
doi = {10.1109/Allerton.2012.6483441},
isbn = {9781467345385},
title = {Revealing Stealthy Attacks in Control Systems},
year = {2012}
}@inproceedings{kn:Teixeira2011,
address = {Milano, Italy},
author = {Teixeira, A and D{\'{a}}n, G and Sandberg, H and Johansson, K H},
booktitle = {18th {IFAC} World Congr.},
title = {Cyber security study of a {SCADA} energy management system: stealthy deception attacks on the state estimator},
year = {2011}
}@article{Shamesetal-automatica-11,
author = {Shames, I. and Teixeira, A.M.H. and Sandberg, H. and Johansson, K.H.},
doi = {10.1016/j.automatica.2011.09.011},
issn = {00051098},
journal = {Automatica},
keywords = {Distributed algorithm,Distributed detection,Fault detection and isolation},
number = {12},
pages = {2757--2764},
title = {Distributed Fault Detection for Interconnected Second-Order Systems},
volume = {47},
year = {2011}
}@inproceedings{kn:Teixeira10,
address = {Atlanta, GA, USA},
author = {Teixeira, A. and Amin, S. and Sandberg, H. and Johansson, K.H. H and Sastry, S.S. S},
booktitle = {49th {IEEE} Conf. Decis. Control},
doi = {10.1109/CDC.2010.5717318},
isbn = {9781424477456},
issn = {01912216},
month = dec,
title = {Cyber Security Analysis of State Estimators in Electric Power Systems},
year = {2010}
}@inproceedings{Shamesetal_SCS_10,
address = {Stockholm, Sweden},
author = {Shames, I and Teixeira, A M H and Sandberg, H and Johansson, K H},
booktitle = {First Work. Secur. Control Syst. CPSWeek},
month = apr,
title = {Distributed Fault Detection for Interconnected Second-Order Systems with Applications to Power Networks},
year = {2010}
}@inproceedings{Teixeira_ACC2010,
address = {Baltimore, MD},
author = {Teixeira, Andre and Sandberg, H and Johansson, K H},
booktitle = {Am. Control Conf.},
doi = {10.1109/ACC.2010.5530638},
isbn = {978-1-4244-7427-1},
month = jun,
pages = {3690--3696},
title = {Networked control systems under cyber attacks with applications to power networks},
year = {2010}
}@inproceedings{kn:Sandberg10,
address = {Stockholm, Sweden},
author = {Sandberg, H and Teixeira, A and Johansson, K H},
booktitle = {First Work. Secur. Control Syst. CPSWeek},
month = apr,
title = {On security indices for state estimators in power networks},
year = {2010}
}